Due to a ruling of the Hamburg Regional Court, access to the "ytdl" website is blocked!
Debian General Resolution: Statement about the EU Legislation "Cyber Resilience Act and Product Liability Directive"
Linux Has Become Complicated And Limiting (GNOME, Wayland, etc)
Ubuntu 23.04 Full Review - An Attempt was Made
Can a Linux distro be partially Closed Source (Proprietary)? YES.
Source:
https://unix.stackexchange.com/questions/129549/can-a-linux-distro-be-closed-source
QUESTION:
According to the GPL licence, which is the one used by the Linux kernel, every modification in the source must be open source too. But, for example, if I create a new OS based on Linux, I develop my own Desktop system and all that stuff, but I don't make any modification to the kernel, does my project need to be open source just by using Linux?
ANSWER:
Here's the preamble to COPYING, included with the kernel source:
"NOTE! This copyright does not cover user programs that use kernel services by normal system calls - this is merely considered normal use of the kernel, and does not fall under the heading of "derived work". [...] note that the only valid version of the GPL as far as the kernel is concerned is this particular version of the license (ie v2, not v2.2 or v3.x or whatever), unless explicitly otherwise stated.
Linus Torvalds"
So, if you want to create your own operating system userland from the ground up, then you can license that part however you like. You can then distribute the whole thing together, and the kernel will be licensed as the kernel is and your userland pieces licensed the way they are. This is not uncommon, since various proprietary systems use the linux kernel (although they would often include other open source pieces too, I think).
What you cannot do is distribute the whole thing together claiming your license applies to the included kernel (unless your license is GPL compatible).
CONCLUSION:
You can license your work as you see fit as long as you respect the Linux Kernel Licence.
And you have the right to license your work as you see fit as long as you respect the Linux Kernel Licence.
So, by accusing any Linux distro of being Closed Source just because the Developers choose to Copyright their Original Work, it's slander at best.
And the same goes for accusing Developers of stealing another distro, just because they choose to Copyright their Original Work.
Source:
https://www.quora.com/Can-a-Linux-distro-be-partly-closed-source-like-95-open-source-or-something
QUESTION:
Can a Linux distro be partly closed source (like 95% open source or something)?
ANSWER:
Sure. Many are (as many include things like firmware for certain devices, and that firmware is often closed source - but not just, for example previously many included Adobe Flash, which again is closed source, or various codecs for playing back multimedia content).
Free software does not mean lack of copyright. Anyone can distribute their source code freely and they can put any restrictions they like on the source code or on the distribution of binaries they built themselves.
We are LINUX MAFIA ARMY!!! If WE CAN'T MAKE MONEY from your Linux Distro WE WILL CALL IT CLOSED SOURCE and DISCREDIT IT!!!

An Open Letter to Intel
Thanks for putting a version of MINIX inside the ME-11 management engine chip used on almost all recent desktop and laptop computers in the world. I guess that makes MINIX the most widely used computer operating system in the world, even more than Windows, Linux, or MacOS. And I didn't even know until I read a press report about it. Also here and here and here and here and here (in Dutch), and a bunch of other places.
I knew that Intel had some potential interest in MINIX several years ago when one of your engineering teams contacted me about some secret internal project and asked a large number of technical questions about MINIX, which I was happy to answer. I got another clue when your engineers began asking me to make a number of changes to MINIX, for example, making the memory footprint smaller and adding #ifdefs around pieces of code so they could be statically disabled by setting flags in the main configuration file. This made it possible to reduce the memory footprint even more by selectively disabling a number of features not always needed, such as floating point support. This made the system, which was already very modular since nearly all of the OS runs as a collection of separate processes (normally in user mode), all of which can be included or excluded in a build, as needed, even more modular.
Also a hint was the discussion about the lisence. I (implicitly) gathered that the fact that MINIX uses the Berkeley license was very important. I have run across this before, when companies have told me that they hate the GPL because they are not keen on spending a lot of time, energy, and money modifying some piece of code, only to be required to give it to their competitors for free. These discussions were why we put MINIX out under the Berkeley license in 2000 (after prying it loose from my publisher).
After that initial burst of activity, there was radio silence for a couple of years, until I read in the media (see above) that a modified version of MINIX was running on most x86 computers, deep inside one of the Intel chips. This was a complete surprise. I don't mind, of course, and was not expecting any kind of payment since that is not required. There isn't even any suggestion in the lisence that it would be appreciated.
The only thing that would have been nice is that after the project had been finished and the chip deployed, that someone from Intel would have told me, just as a courtesy, that MINIX was now probably the most widely used operating system in the world on x86 computers. That certainly wasn't required in any way, but I think it would have been polite to give me a heads up, that's all.
If nothing else, this bit of news reaffirms my view that the Berkeley license provides the maximum amount of freedom to potential users. If they want to publicize what they have done, fine. By all means, do so. If there are good reasons not to release the modified code, that's fine with me, too.
Yours truly,
Andrew S. Tanenbaum
---
Note added later: Some people have pointed out online that if MINIX had a GPL license, Intel might not have used it since then it would have had to publish the modifications to the code. Maybe yes, maybe no, but the modifications were no doubt technical issues involving which mode processes run in, etc. My understanding, however, is that the small size and modular microkernel structure were the primary attractions. Many people (including me) don't like the idea of an all-powerful management engine in there at all (since it is a possible security hole and a dangerous idea in the first place), but that is Intel's business decision and a separate issue from the code it runs. A company as big as Intel could obviously write its own OS if it had to. My point is that big companies with lots of resources and expertise sometimes use microkernels, especially in embedded systems. The L4 microkernel has been running inside smartphone chips for years. I certainly hope Intel did thorough security hardening and testing before deploying the chip, since apparently an older version of MINIX was used. Older versions were primarily for education and newer ones were for high availability. Military-grade security was never a goal.
Second note added later: The online discussion got completely sidetracked from my original points as noted above. For the record, I would like to state that when Intel contacted me, they didn't say what they were working on. Companies rarely talk about future products without NDAs. I figured it was a new Ethernet chip or graphics chip or something like that. If I had suspected they might be building a spy engine, I certainly wouldn't have cooperated, even though all they wanted was reducing the memory footprint (= chip area for them). I think creating George Orwell's 1984 is an extremely bad idea, even if Orwell was off by about 30 years. People should have complete control over their own computers, not Intel and not the government. In the U.S. the Fourth Amendment makes it very clear that the government is forbidden from searching anyone's property without a search warrant. Many other countries have privacy laws that are in the same spirit. Putting a possible spy in every computer is a terrible development.
https://www.cs.vu.nl/~ast/intel/
Distrobox - Use any Linux distribution inside your terminal.
We are LINUX MAFIA ARMY!!! If YOUR LINUX DISTRO is better than ours we will NEVER REVIEW IT, we will CALL IT SCAM and SLANDER IT!!!

We are LINUX MAFIA ARMY!!! If YOUR LINUX DISTRO is better than ours WE WILL CALL IT BLOAT and DISCREDIT IT!!!

GNOME propaganda machine is heavily funded by companies.
GNOME is a free product made by GNOME Foundation, which is a non-profit company founded in 2000 by companies such as IBM, Sun Microsystems, Compaq and Red Hat. On its advisory board there are many big players, like Google, Canonical, Debian, SUSE and System76. Its annual income has been around 1 million dollars since 2018. Red Hat estimated that 70% of the code committed for GNOME comes from paid participants who work for other companies. So essentially this is not a bunch of volunteer geeks who like to code in the night just for fun, but rather a company with direct and indirect employees, managers, directors, deadlines and a product that needs to make a profit for its investors and shareholders.
It is important to remember all that when talking about GNOME...
GNOME Linux — A Complete Disaster?
Gnome 40 - The anti-desktop desktop
Download XSnow and celebrate in your screen!
We are LINUX MAFIA ARMY!!! We do ONLINE MOB/SWARM CHARACTER ASSASSINATIONS to anyone who DOES NOT SUBMIT TO US!!!

We are LINUX MAFIA ARMY!!! We have 1000's of THUGS working at the BACKBONE OF THE INTERNET to promote our MONEY GRAB OPERATIONS!!!
We are LINUX MAFIA ARMY!!! We preach FOSS just to MAKE MONEY out of your Love for Linux!!! You are such a SUCKER!!!

We are LINUX MAFIA ARMY!!! If WE CAN'T MAKE MONEY from your Linux Distro WE WILL CALL IT BLOAT and DISCREDIT IT!!!

A Minimum Viable Computer, or Linux for $15!
We are LINUX MAFIA ARMY!!! We DELETE reddit COMMENTS that refer to Linux Distros that go against our MONEY GRAB OPERATIONS!!!
We are LINUX MAFIA ARMY!!! We DELETE reddit COMMENTS that refer to Linux Distros WE DON'T MAKE MONEY FROM!!!
Linux Tutorials and the LINUX MAFIA ARMY...
If people don't understand the tutorial because the tutorial is intentionally wrong or intentionally incomplete, then people are going to leave Comments.
Comments are Engagement.
Engagement is Views.
Views are Cookies Spying on You and Selling your Personal Web Browsing Data to 1000's of Capitalist Companies.
Selling everybody's Personal Web Browsing Data to 1000's of Capitalist Companies is MONEY.
Making Money this way is the LINUX MAFIA ARMY way.
- root
We are LINUX MAFIA ARMY!!! You will only use the LINUX DISTROS we tell you to use!!!
In defence of swap: common misconceptions
Wise words for Developers
- Animal
"I'm personally not a fan of removing useful things for the sake of "simplicity" or changing things just for the sake of changing them."
- AxelF
"Usability should not be sacrificed in the name of "simplicity" because unusable is not even simple. It's unusable."
- root
Source
Concerning Free Open Source Software (FOSS)
Philosophically and ethically we agree but every day practicality needs things get done.
We support FOSS but in the real world 99% of Devices, Appliances, Machinery and Vehicles YOU USE run on Proprietary Software.
The Computer or Tablet or Phone you are using right now to Preach FOSS runs on Proprietary Software (Embedded in the Hardware or not).
This is pure hypocrisy.
We agree that FOSS is good but we need things get done and if FOSS does not suit us we'll use whatever software does the job.
That's what FOSS Fanatics don't get. Users need things get done. Now.
Mac, iPhone and iPad run on Proprietary Software and still they changed the world and gave us tremendous power.
Proprietary Software is not always about removing or limiting our Freedoms and our Rights.
It can be about User Experience Consistency, Quality Control and Stability.
Not all proprietary Applications are full of DRM, spies and sell your data for advertising purposes.
FOSS Applications can also be full of DRM, spies and sell your data for advertising purposes.
Source
Distrowatch is NOT a Measure for Distributions Popularity
MNT Reform: The Much More Personal Computer
"Linux Community" and the Linux Mafia Army
It's no secret that 99% of all those "Linux Community Websites & Linux YouTube Channels & Linux IRC Chat Channels", promote 5-10 Linux Distros out of 100's. This is not random.
And it goes deeper that that. The hostile behaviour of this "Linux Mafia Army" when you talk about other distros than the ones they push, is classic...
All those "Linux Community Websites & Linux YouTube Channels" sell your browsing data to 1000's of capitalist companies by spying on you via Cookies, so even in most Linux distros (FOSS or not) you are the product...
I am not saying that it's bad to want to make money, but if at the same time you are preaching Internet Freedom and FOSS, it's a bit hypocritical at best.
So, don't lecture us about the so called "Linux Community".
We know the subversive and covert tactics of your "Dark Web Gang": Online Mob/Swarm Misinformation, Online Mob/Swarm Slandering, Online Mob/Swarm Character Assassination, Online Mob/Swarm Psychological Operations, Online Mob/Swarm Sabotage.
You may have positioned yourself at the backbone of the internet, pulling strings from the shadows, but you are not invisible.
~ root
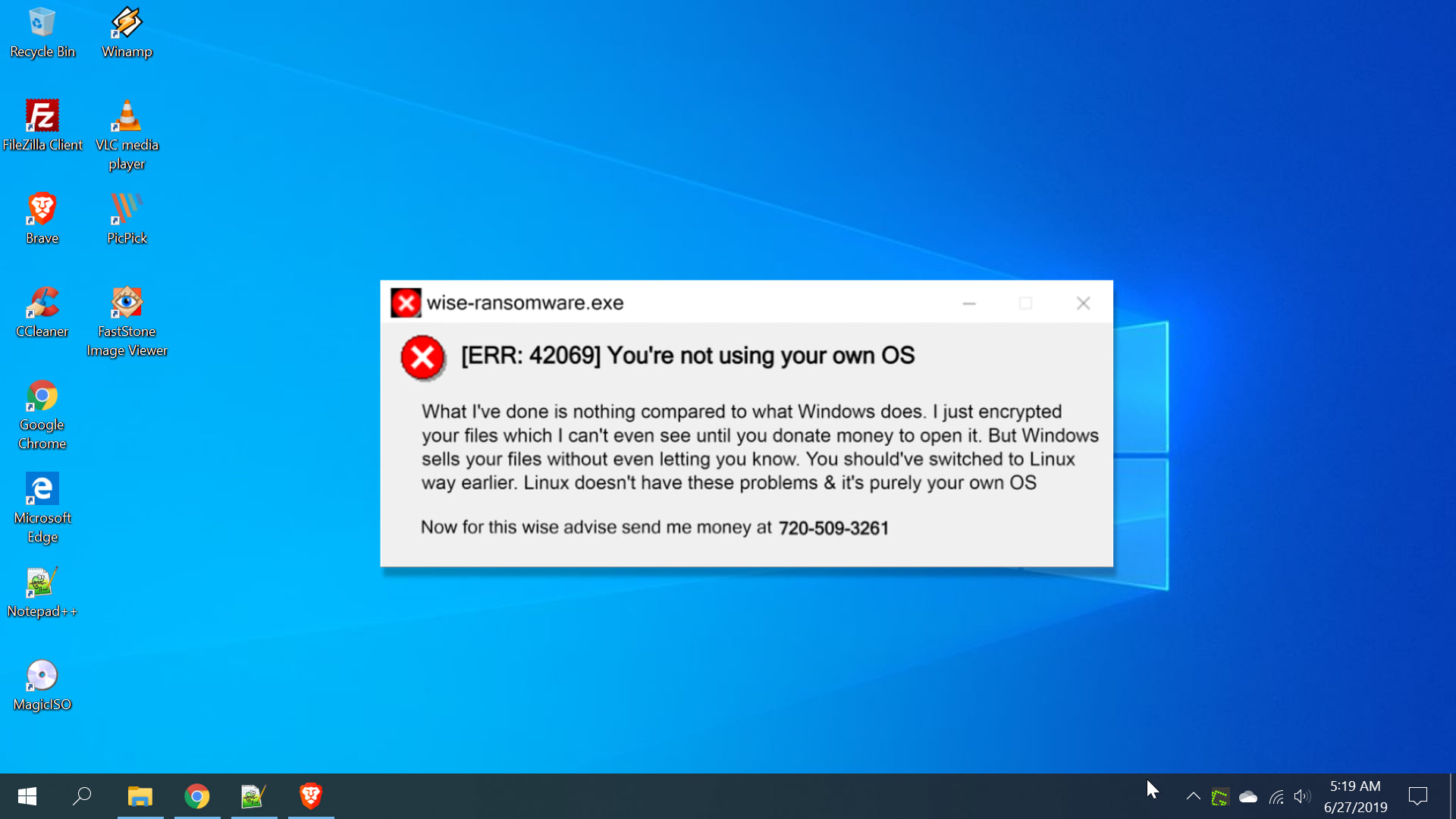
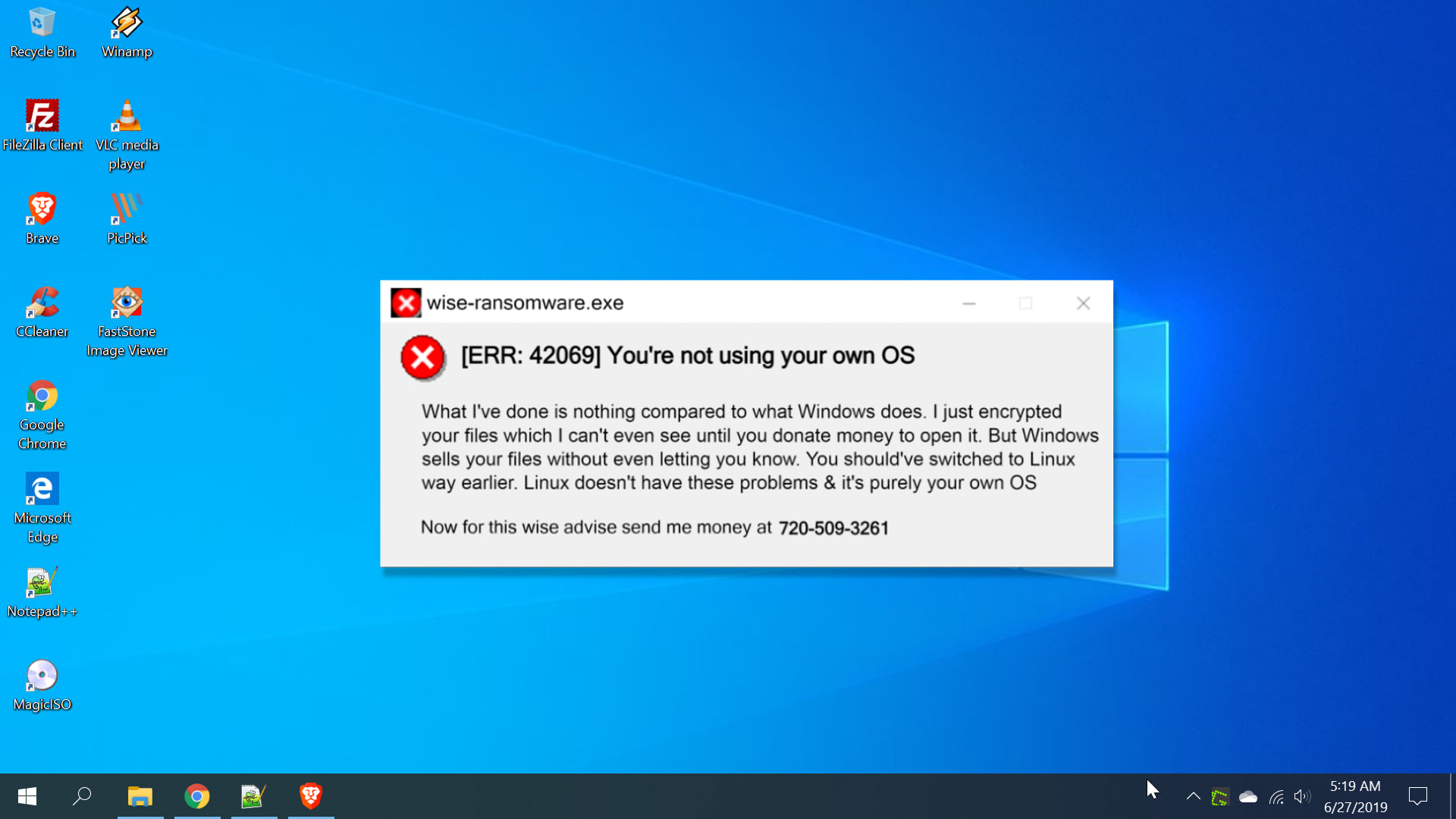
Anatomy of a Linux Ransomware Attack

Here are our top tips and advice for protecting against Linux Ransomware:
Backup critical files and diversify the storage media to avoid a single point of failure (SPOF). This won’t prevent an attack, but can mitigate potential damage.
Keep servers and endpoints up to date to ensure that they use the latest security patches.
Implement the principle of least privilege for user accounts.
Monitor network activity and system logs closely.
Keep tabs on event logs to identify anomalous behavior before it causes harm.
Use a combination of IP filtering, an intrusion detection system (IDS) and an intrusion prevention system (IPS).
Use Linux security extensions that control and restrict access to data or network resources.
Implement robust network segmentation and data compartmentalization to minimize the impact of a potential ransomware attack.
Audit systems regularly.
More on: https://linuxsecurity.com/features/anatomy-of-a-linux-ransomware-attack
Hive ransomware now encrypts Linux and FreeBSD systems
Computer Operating Systems where born to be...
Linux/Unix: Born to be root
Windows: Born to re boot
Why iLinux OS is not listed in DistroWatch?
Julian Assange: Debian Is Owned By The NSA?
(For Debian watch from 20:20)
https://igurublog.wordpress.com/2014/04/08/julian-assange-debian-is-owned-by-the-nsa/